As ThoughtSpot accelerates into its next phase of growth with AI-powered analytics, we are more committed than ever to providing value to our enterprise customers. In recent months, we delivered several features and enhancements designed specifically for your IT and Security Operations Administrators, who are at the forefront of provisioning and managing users and access to business objects.
As ThoughtSpot rapidly scales to meet the growing needs of our customers, ensuring robust data security for your organization remains paramount. Traditional Identity and Access Management (IAM) systems often struggle to keep pace with the complexities of managing a vast number of users, access permissions, and evolving compliance regulations. This can lead to several critical challenges:
Identity sprawl: Managing numerous identities and access privileges across various systems can be overwhelming and error-prone.
Security risks: Weak passwords and compromised credentials can become gateways for unauthorized access and data breaches, jeopardizing sensitive information.
Compliance labyrinth: Keeping up with the ever-changing landscape of data privacy regulations such as GDPR and CCPA is complex and resource-intensive.
Inefficient user management: Manual user provisioning and de-provisioning processes are time-consuming and susceptible to human error.
Several notable security incidents underscore the risks of weak IAM practices. In 2013–2014, Yahoo suffered one of the largest data breaches in history, affecting 3 billion accounts when attackers exploited weak account recovery and authentication tools. Equifax’s 2017 breach exposed sensitive data of 147 million people through an unpatched vulnerability in a web application, exacerbated by inadequate access controls that allowed attackers to retain prolonged access. LinkedIn’s 2012 breach exposed over 150 million accounts due to weak password encryption (SHA-1) and insufficient multi-factor authentication. Data infrastructure providers have encountered security challenges in 2024, making this a topic of heightened interest amongst customers.
These cases highlight the need for robust security practices, such as multi-factor authentication (MFA), strong password hashing and policies, and consistent security updates in web applications. At ThoughtSpot, we’ve proactively addressed these challenges by releasing Enhanced Identity and Access Management with IAM version 2 (IAM v2).
Introducing Enhanced Identity and Access Management with IAM v2
To address the prevailing challenges in the user administration and security domain, we’re excited to introduce Enhanced IAM with IAM v2, a comprehensive solution to streamline user management and enhance security. IAM v2 equips your enterprise organization with essential tools to implement stronger password policies, enforce regular password rotation, and enable multi-factor authentication (MFA).
ThoughtSpot IAM v2 is built in partnership with Okta, a well-known industry leader for Identity and Access Management for enterprise-grade security and compliance. ThoughtSpot Cloud architecture now includes ThoughtSpot-managed Okta as a service provider for its Cloud instances. ThoughtSpot leverages Okta features like Multi-Factor Authentication and Strong Password Policies in its IAM v2 implementation on cloud deployments.
The following figure illustrates the high-level architecture of how ThoughtSpot is integrated with ThoughtSpot-hosted Okta:
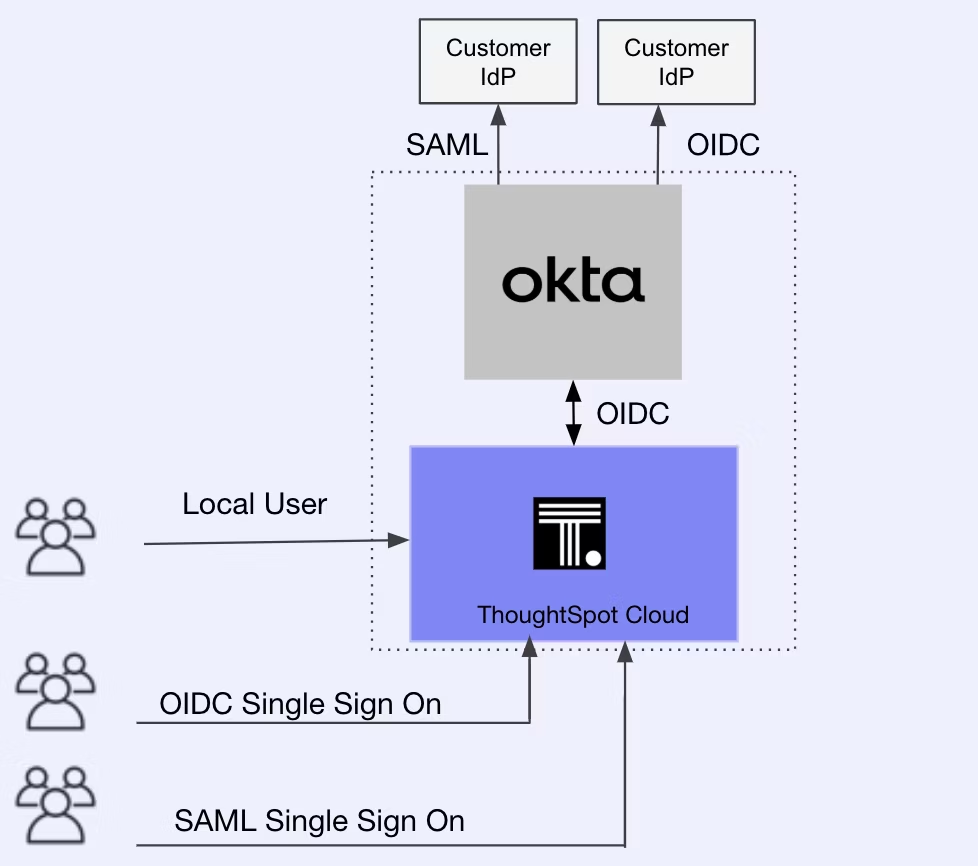
Figure 1. ThoughtSpot and Okta integration
Lifecycle of a login request with IAM v2
The following figure illustrates the lifecycle of a login request:
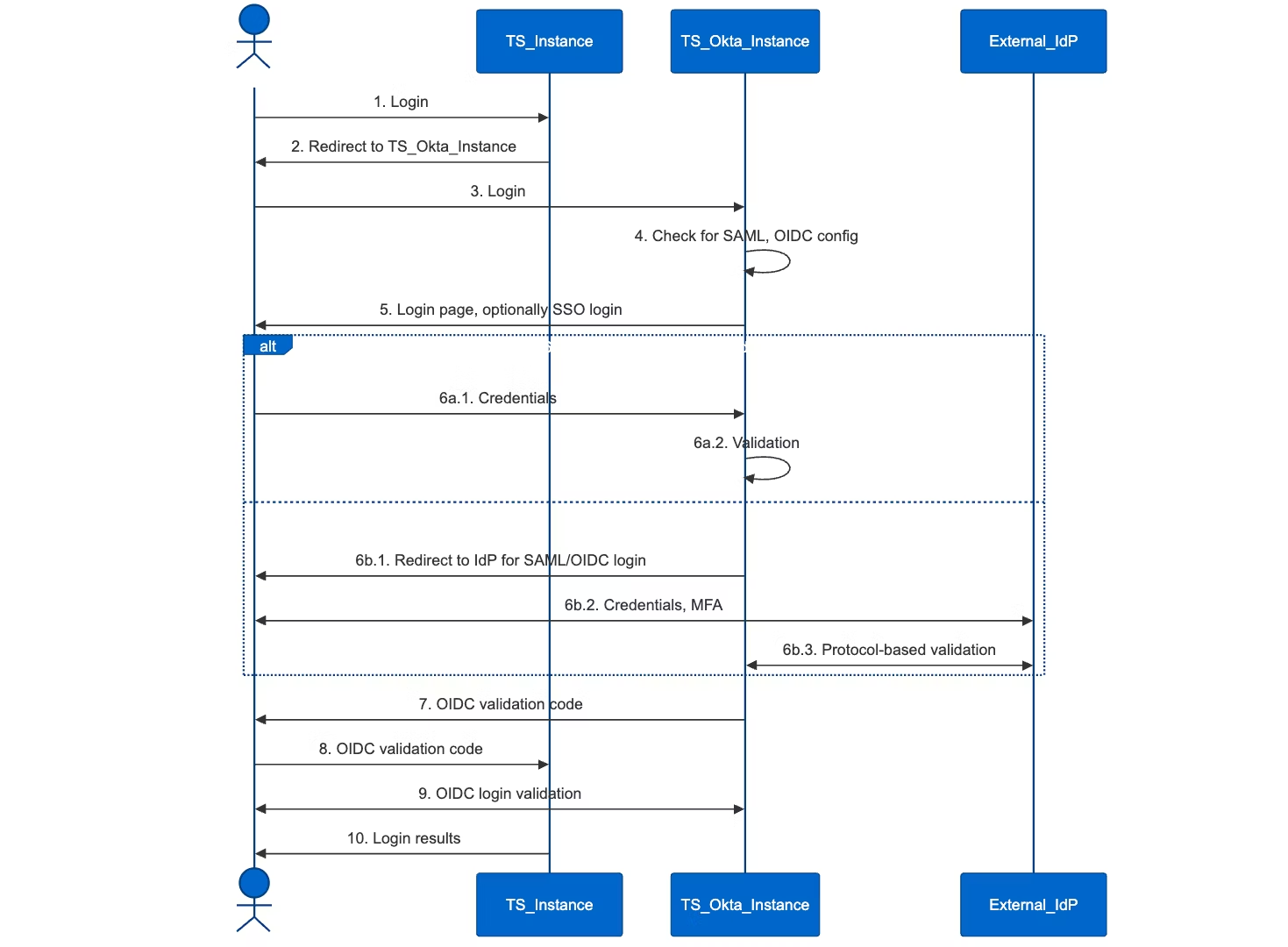
Figure 2. Lifecycle of a login request
A typical login workflow with OpenID Connect (OIDC) protocol involves the following steps:
1. TS_Client initiates login with TS_Instance
A ThoughtSpot client (TS_Client) sends a login request to the ThoughtSpot instance (TS_Instance).
2. TS_Instance redirects TS_Client to TS_Okta_Instance
TS_Instance responds by redirecting TS_Client to TS_Okta_Instance, a ThoughtSpot-dedicated Okta instance for authentication. This is an initial step in the OIDC Authorization Code Flow, where the client is redirected to the authorization server (Okta).
3. TS_Client attempts login with TS_Okta_Instance
TS_Client makes a login request to TS_Okta_Instance, entering the OIDC flow outlined in RFC 6749 (OAuth 2.0 Authorization Framework) and RFC 8414 (OAuth 2.0 Authorization Server Metadata).
4. TS_Okta_Instance checks for SAML or OIDC configuration
TS_Okta_Instance verifies whether to use the locally-saved user credentials, Security Assertion Markup Language (SAML), or OIDC protocols based on the configurations.
Note: Between TS_Instance and TS_Okta_Instance, the OIDC protocol is used, and TS_Okta_Instance will use the authorization code to issue tokens after successful authentication.
5. TS_Okta_Instance presents a login page with optional Single Sign-On (SSO) option
TS_Okta_Instance returns a login page to TS_Client with options to log in using credentials or use SSO.
6. TS_Client may proceed to login with either local or SSO
a. Local user login with credentials
TS_Client submits credentials directly to TS_Okta_Instance.
TS_Okta_Instance validates the credentials and, if valid, proceeds to issue an authorization code in the OIDC flow.
b. SSO login
TS_Okta_Instance redirects TS_Client to an external Identity Provider (External_IdP) for SAML/OIDC login.
TS_Client interacts with External_IdP to provide credentials and may complete multi-factor authentication (MFA).
Upon successful authentication, External_IdP performs protocol-based validation with TS_Okta_Instance, completing the SAML/OIDC exchange.
7. TS_Okta_Instance issues an OIDC authorization code to TS_Client
Upon successful authentication, TS_Okta_Instance issues an authorization code to TS_Client. According to the OIDC specification in RFC 6749, this code is a short-lived token that allows the client to request an ID token and access the token without exposing the user’s credentials.
8. TS_Client sends the authorization code to TS_Instance
TS_Client sends this authorization code to TS_Instance. TS_Instance will act as a backend component to exchange this code for an ID token and access token.
9. TS_Client and TS_Okta_Instance complete the OIDC login validation
Using the authorization code, TS_Instance makes a request to TS_Okta_Instance’s token endpoint to exchange the authorization code for tokens (ID token, access token). This step follows the OIDC Authorization Code Flow as defined in RFC 6749 and OIDC Core.
TS_Okta_Instance validates the authorization code and, if successful, responds with tokens that TS_Instance can use to authenticate the user.
10. TS_Instance returns login results to TS_Client
Finally, TS_Instance completes the OIDC login process by responding with login results to TS_Client, indicating successful authentication and access rights.
The OIDC Authorization Code Flow used here enhances security by keeping user credentials from being directly exposed to the client. Furthermore, the per-application secret shared between TS_Instance and TS_Okta_Instance is stored securely in a vault with Role-Based Access Control (RBAC) policies implemented per TS_Instance. This ensures that only authorized entities can access sensitive information and influence user login decisions. For more technical details, refer to the OIDC specification in the OpenID Connect Core 1.0 document.
Advantages of Enhanced Identity and Access Management with IAM v2
Enhanced Identity and Access Management with IAM v2 provides the following advantages:
Enterprise-grade IAM mechanism for modern cloud apps with Okta: InfoSec policies within organizations are easily compliant with an industry standard identity service like Okta for ThoughtSpot Cloud.
SSO support with SAML 2.0 and OIDC: ThoughtSpot is now protocol-agnostic of the Identity Provider (IdP) being used in customer organizations, as long as ThoughtSpot integrates with Okta using OIDC. All IdP responses will be processed by ThoughtSpot-managed Okta.
Modern user management practices, like self-serve password management, user activation, and reset and forgot password flows: With Enhanced Identity and Access Management, the cluster administrator is no longer the single point of contact for user management. ThoughtSpot now supports modern user management flows, like allowing the user to activate their account by setting their own passwords, or going through the forgot password flow to reset their passwords. However, we continue to allow our TSE customers to manage their users via their automation using REST APIs.
MFA support for local users: MFA will be fully supported for local users, offering reduced risk of compromised credentials and enhanced protection against evolving security threats and attacks. Given the rise of such threats, MFA has become an essential layer of defense for enterprises today.
Advanced password management: Okta’s allowance of advanced password management and policies enables greater flexibility and security per instance for ThoughtSpot Cloud customers.
Support for Analyst Studio: Analyst Studio support is available exclusively with IAM v2.
Support to configure a separate IdP per Organization enabled with multi-tenancy with Orgs is supported exclusively with IAM v2.
Faster rollout of advanced identity management and security features
How customers will be enabled with Enhanced Identity and Access Management
All new ThoughtSpot Cloud customers will be enabled with IAM v2. Existing customer instances will be migrated to IAM v2 during maintenance or upgrade windows.
All customers need to run through the necessary pre-migration steps to check cluster readiness. The current IAM mechanism will be deprecated with due notification.
What changes for ThoughtSpot customers
Please note the following changes:
Email is now a mandatory attribute for all users on ThoughtSpot Cloud. Administrators must ensure that the email property is updated for all users, considering that users will now set or /reset their passwords.
Login URL redirect to an Okta-hosted URL requires customers who allowlist their ThoughtSpot instance URL to add URLs to allowlists.
Post migration, customers using SAML need to change a couple of attributes on their IdP to ensure that responses are directed to ThoughtSpot Okta instead of their ThoughtSpot instance, and then click Submit on the IdP page on the ThoughtSpot UI to switch over to using ThoughtSpot Okta instead of the current IAM mechanism.
ThoughtSpot users need to have their login credentials handy to re-enter their credentials post migration, because browser caching of the same will not work due to the change in redirect URLs.
ThoughtSpot administrators and users must be educated about activation flows and reset password flows.
TSE customers should see no change to their automation scripts. API changes, if any, will be announced in the API changelog.
Conclusion
ThoughtSpot's Enhanced Identity and Access Management with IAM v2 equips you with a more robust, modern, and secure user management experience aligned with the latest industry standards. By partnering with Okta, ThoughtSpot brings you seamless integrations with SSO protocols like SAML 2.0 and OIDC, improved multi-factor authentication (MFA) capabilities, and comprehensive user management flows, including self-service password reset and account activation. These capabilities strengthen data security across your organization and simplify compliance with rigorous data privacy regulations.
As a ThoughtSpot customer, Enhanced Identity and Access Management with IAMv2 means faster access to new identity and access management features, greater control over security configurations, and streamlined support for end-user access—all crucial for safeguarding data and managing access efficiently.
With more IAM enhancements on the way, ThoughtSpot is committed to providing secure, enterprise-grade analytics and helping your IT and Security Operations Administrators navigate today’s complex security landscape.
If you’re new to ThoughtSpot, learn more about our partnership with Okta, and schedule a live demo today!










